Secure Gateways
What are Secure Gateways?
The n2x.io Secure Gateway is a powerful component that combines load balancing capabilities with an Identity-Aware Proxy (IAP). This enables several key functionalities:
-
Centralized Access Control: The secure gateway offers a single point of control for managing application access permissions.
-
Enhanced Security: The IAP functionality within the gateway meticulously authenticates and authorizes users before granting access, safeguarding your network.
-
Granular Control with Tags: n2x.io utilizes a
tag-basedauthorization system. This allows you to define fine-grained access policies based on tags assigned to users, devices, and resources. -
Secure Public Access: The secure gateway, in conjunction with a (virtual server), facilitates controlled public access to specific resources. This enables authorized external users to securely connect without compromising internal network security.
Identity-Aware Proxy (IAP)
The IAP provides a centralized authorization layer for applications accessed via HTTPS from the internet. Unlike traditional methods, IAP doesn't require any client-side software or agents to be installed on user devices. This streamlines user access and eliminates the need for complex client-side configurations.
Set Up a Secure Gateway
There are two main steps required to configure a Secure Gateway:
Warning
Only Account Administrators or Admin Users can manage virtual servers.
- Create a Virtual Server with authentication enabled.
- Add Node Services to the Virtual Server.
Once the (virtual server) is configured, the Secure Gateway authenticates the users accessing the public URL using the n2x.io proxy user credentials.
Here's an example virtual server configuration:
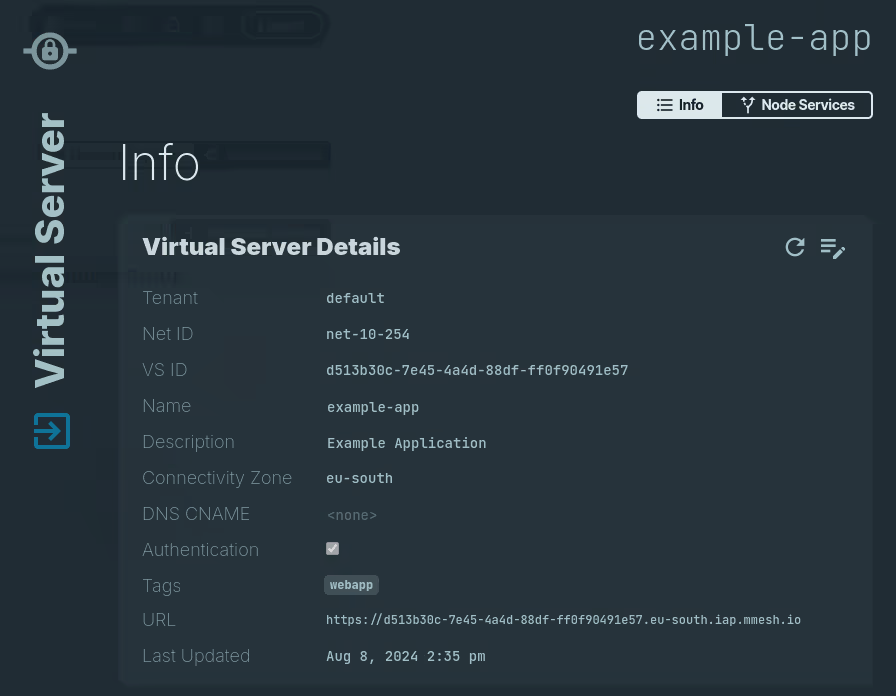
Success
Once the virtual serveris configured, the Secure Gateway authenticates the users accessing the public URL using the n2x.io proxy user credentials.
Granting Secure Access to Your Application
This section details how to securely share access to your publicly exposed application with authorized individuals within your organization.
1. Creating an ACL
The Account Administrator needs to create an ACL and associate it with the tag(s) that identify the applications you want to share access to.
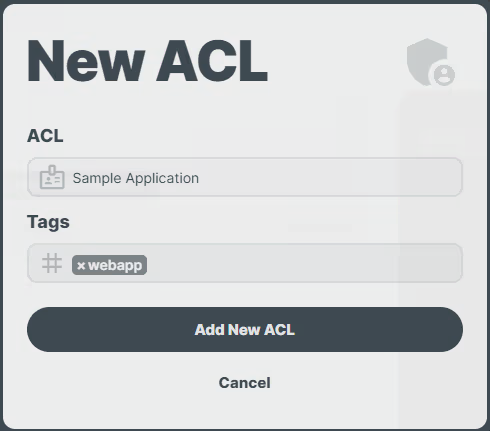
2. Creating Proxy Users and Grantting Access
For each person needing access to the application, the Account Administrator needs to create a new proxy user account using their email address. Assigning the ACL you created in the previous step (e.g., Sample Application Access) to each user in the process.
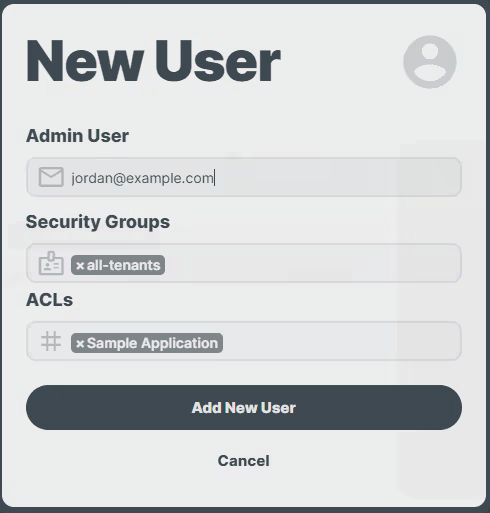
Success
These steps grants them the necessary permissions to access the application through the Secure Gateway.