How to Connect Directly to your Azure VNet
This tutorial empowers you to deploy an n2x-node within an Azure Virtual Network and configure it to directly access existing Azure Virtual Machines in a private subnet. Streamline your workflow and prioritize security by eliminating the need for a bastion host and enabling direct, encrypted private access from any node in the n2x.io network topology.
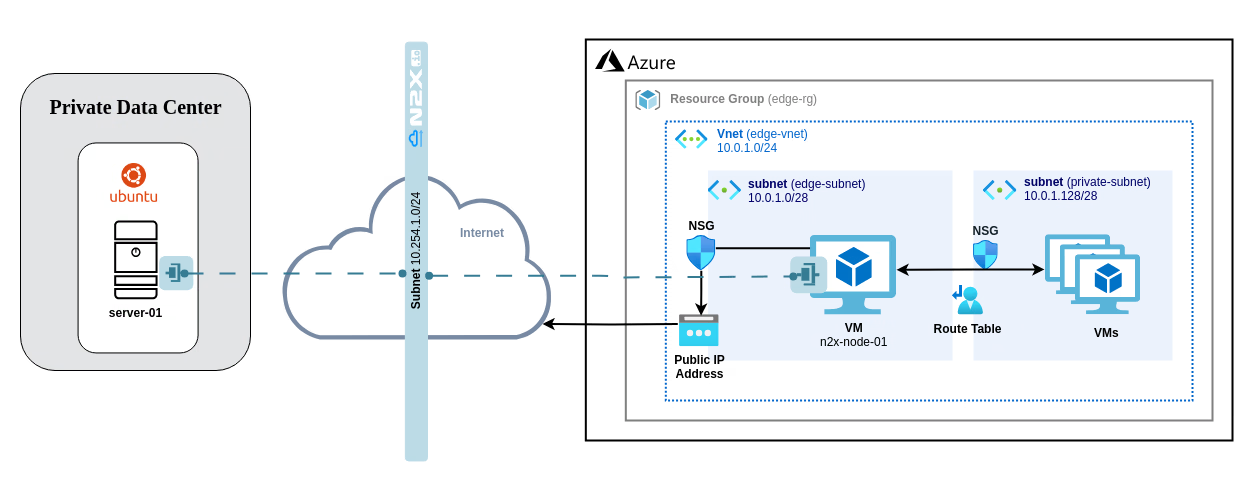
Here is the high-level overview of tutorial setup architecture:
Note
This guide demonstrates how to deploy a single n2x-node within a single availability zone. To achieve high availability failover, multiple n2x-nodes can be deployed across multiple availability zones and configured to export the same routes.
In our setup, we will be using the following components:
-
Azure Virtual Network is a service that provides the fundamental building block for your private network in Azure. For more info please visit the Azure Documentation
-
n2x-node is an open-source agent that runs on the machines you want to connect to your n2x.io network topology. For more info please visit n2x.io Documentation.
Before you begin
In order to complete this tutorial, you must meet the following requirements:
-
An Azure account with an active subscription.
-
A n2x.io account and one subnet with
10.254.1.0/24prefix.
Note
Please note that this tutorial uses a Linux OS with an Ubuntu 24.04 (Noble Numbat) with amd64 architecture.
Step-by-step Guide
Step 1 - Deploying a n2x-node in Azure
This step-by-step guide, will help you set up an n2x-node in Azure. It covers the creation of all the necessary infrastructure within Azure, including a resource group (RG), virtual network (VNet), subnet, network security group (NSG), and a virtual machine (VM).
An additional step is required
You'll need to add an outbound rule to the n2x-node-nsg network security group allowing all traffic to the 10.0.1.128/28 private subnet.
Step 2 - Configuring n2x-node to export VNet CIDR
Before configuring n2x-node-01 to export VNet CIDR, we need to enable IP forwarding on both the Azure VM and its associated Network Interface Card (NIC). This allows the VM to forward incoming IPv4 packets. Here's how to do it:
Now, to make the VNet CIDR available on your n2x.io subnet we need to configure the n2x-node-01 to export this CIDR. For this, we need to edit /etc/n2x/n2x-node.yml and add the following configuration:
# network routes behind this node (optional)
routes:
export:
- <VNet CIDR>
import:
Info
Replace <VNet CIDR> with the VNet CIDR value, in this case is 10.0.1.0/24.
Restart the n2x-node service for this change to take effect:
sudo systemctl restart n2x-node
Step 3 - Deploying Private Azure Virtual Machines
Before creating the Private Azure Virtual Machines we need to create a private subnet and some additional resources:
-
Add the
private-subnetin theedge-vnetVnet as described in the following table. For more information, see Add a Subnet:Subnet Settings
Subnet Name IPv4 address range Starting address Size NAT gateway NSG Route table private-subnet 10.0.1.0/24 10.0.1.128 /28 none none none 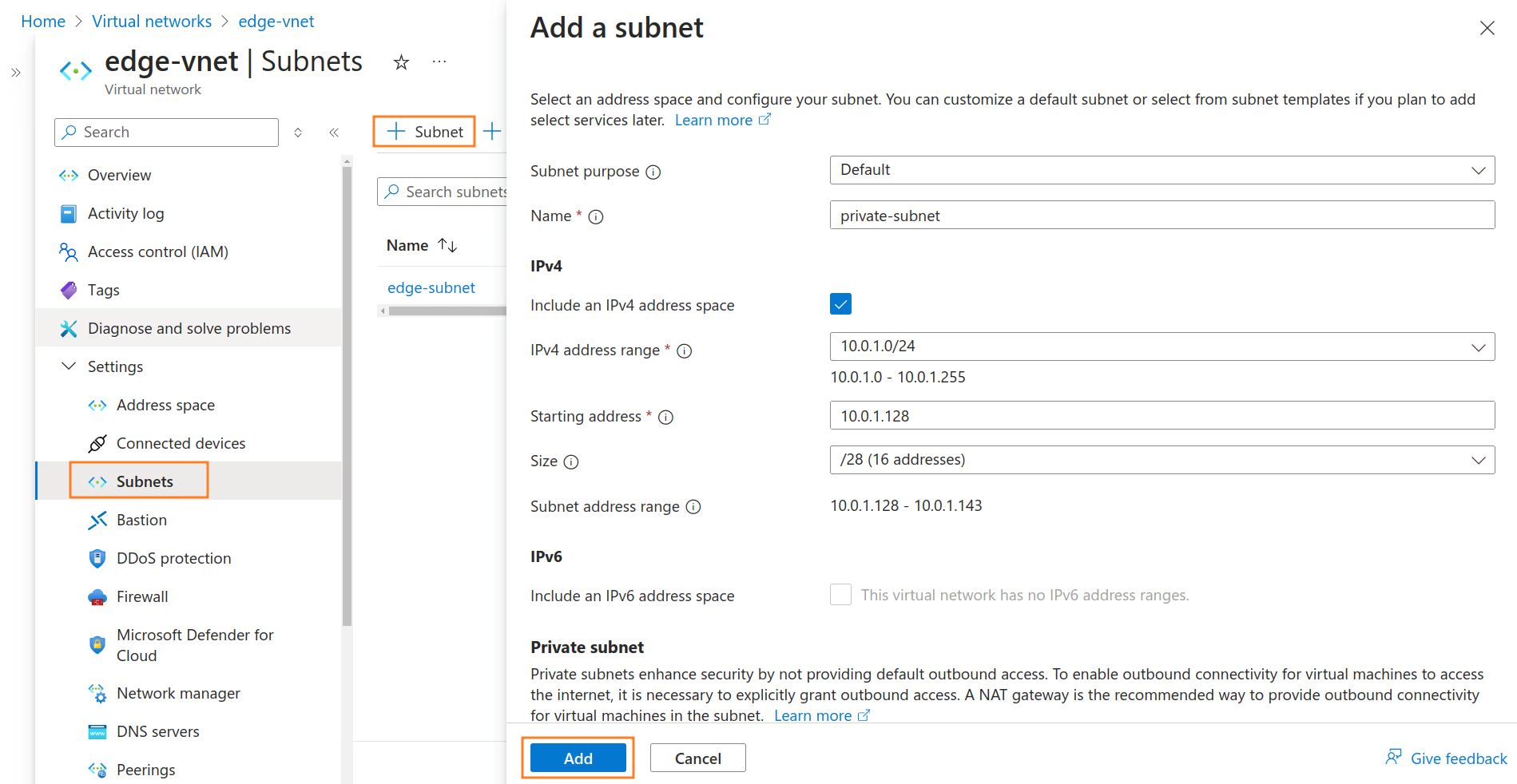
-
Create a routing table for the
private-subnetand add a new route in the route table with the destination10.254.1.0/24(n2x.io subnet CIDR) vía IP address ofn2x-node-01VM. For more information, see Manage Route Table.Routing Table Settings
Resource Group Region Name Propagate gateway routes edge-rg East US private-subnet-rt Yes 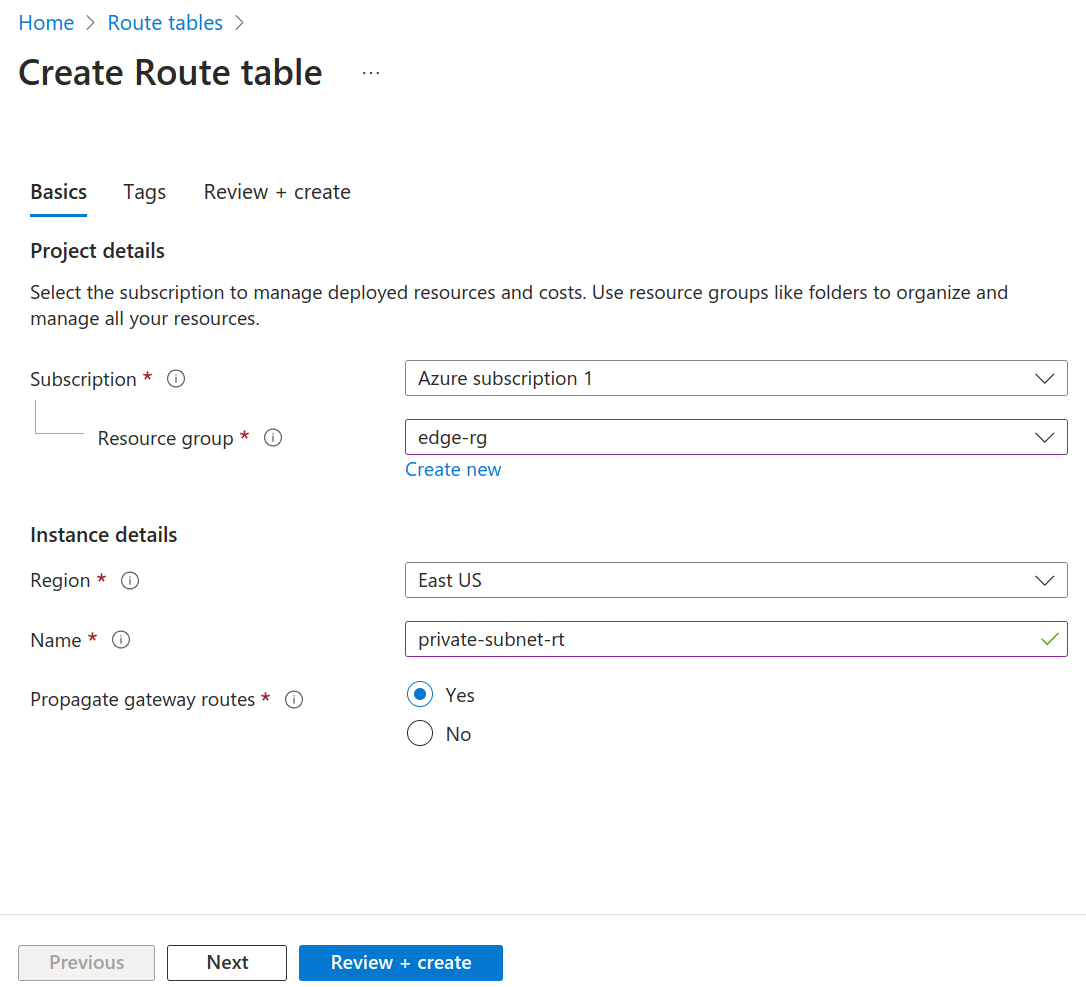
Route Settings
Route name Destination Type Destination IP addresses / CIDR Range Next hop type Next hop address n2x-net-route IP Addresses 10.254.1.0/24 Virtual appliance 10.0.1.4 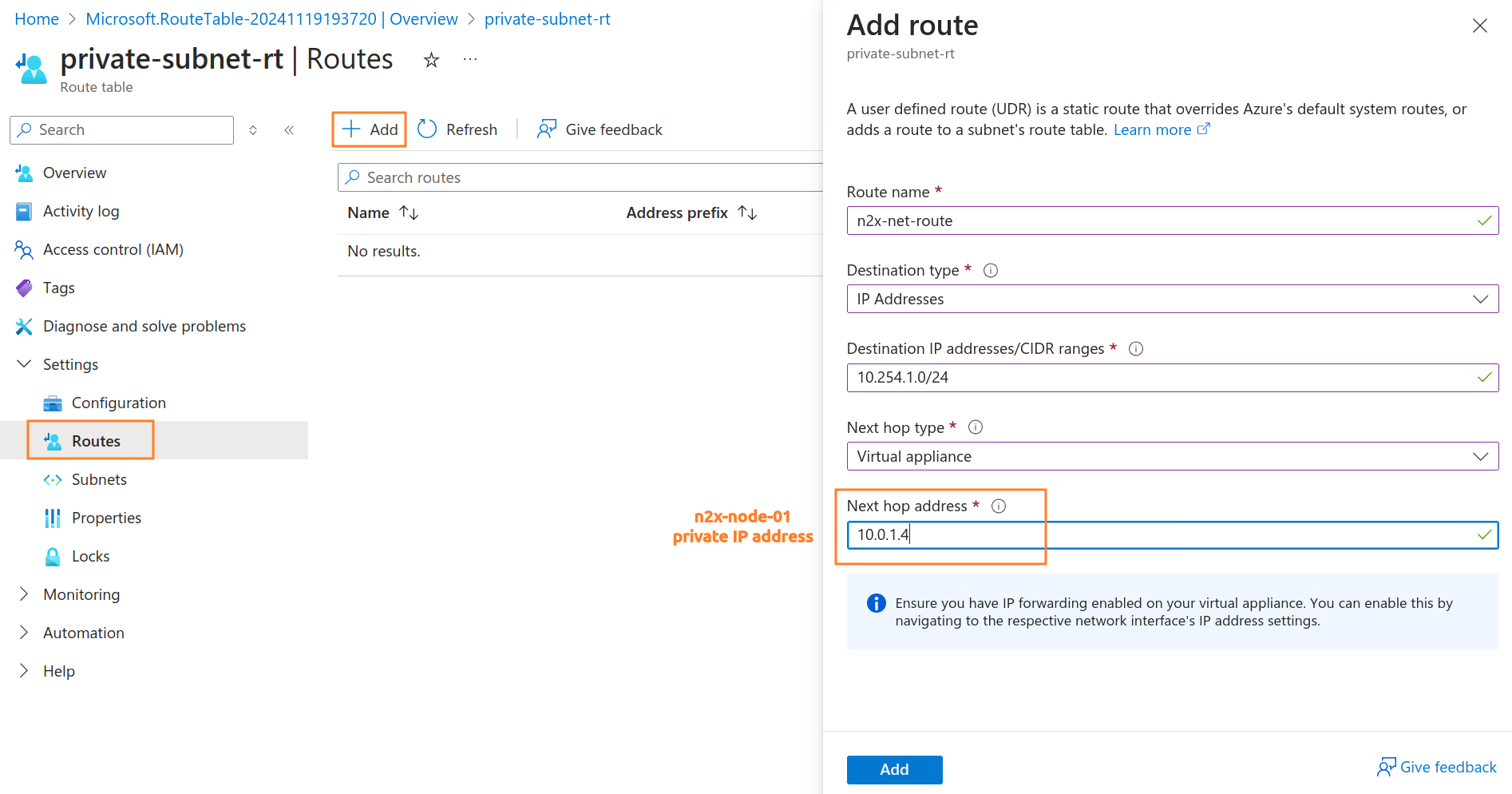
-
Create a network security group
private-vms-nsgthat allows ICMP and SSH access from the n2x.io subnet10.254.1.0/24. For more information, see Manage network security groups.Network Security Group Settings
Resource Group Region Name edge-rg East US private-vms-nsg 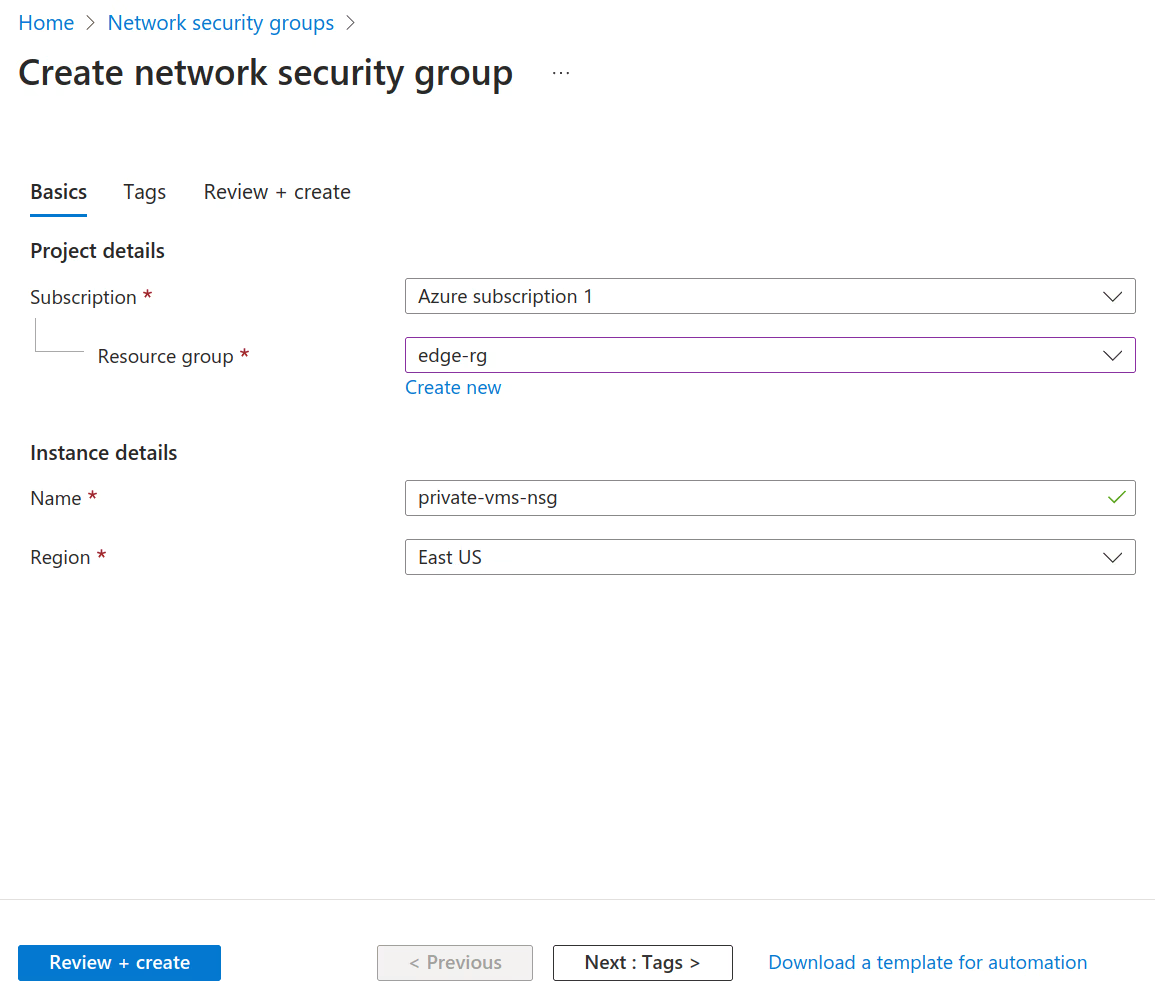
Network Security Group Rules
Rule Source Destination Service Protocol Action Inbound 10.254.1.0/24 Any Custom ICMPv4 Allow Inbound 10.254.1.0/24 Any SSH TCP Allow 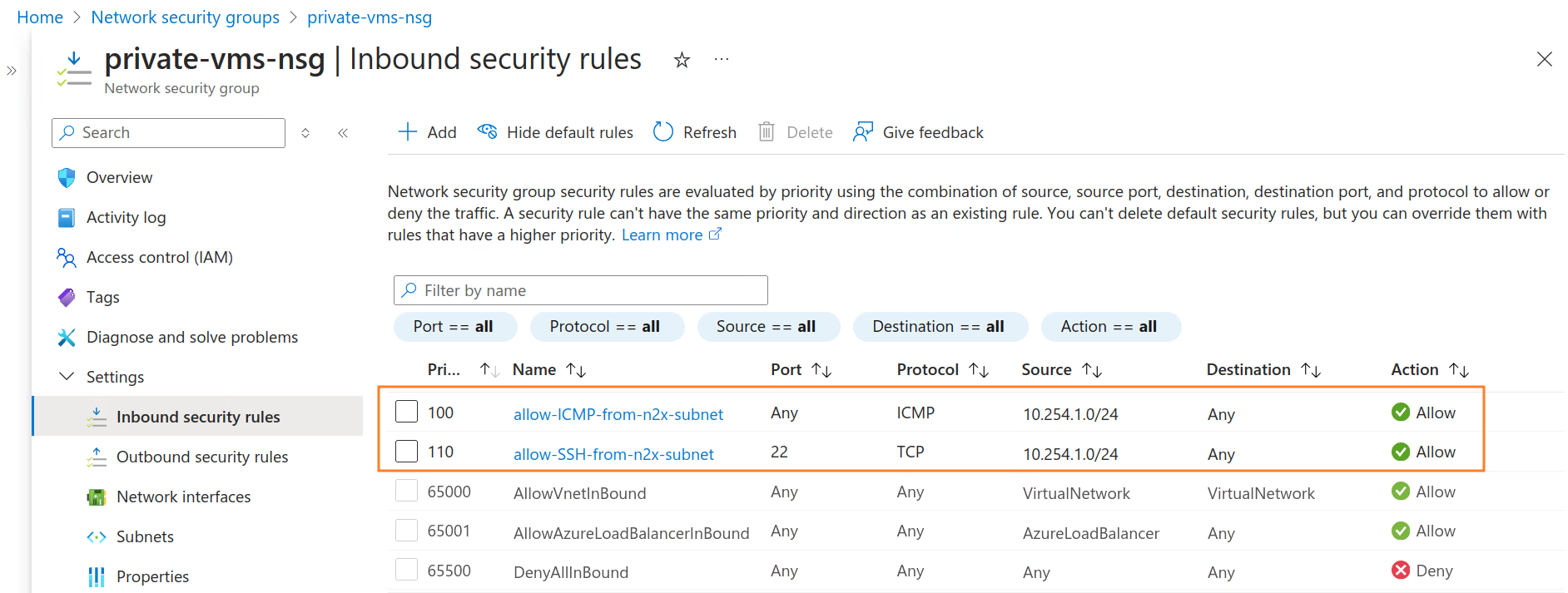
-
The next step involves associating the previously configured
private-subnet-rtroute table andprivate-vms-nsgnetwork security group with theprivate-subnet. To do this, navigate to the Virtual Networks section, selectedge-vnetand edit theprivate-subnet: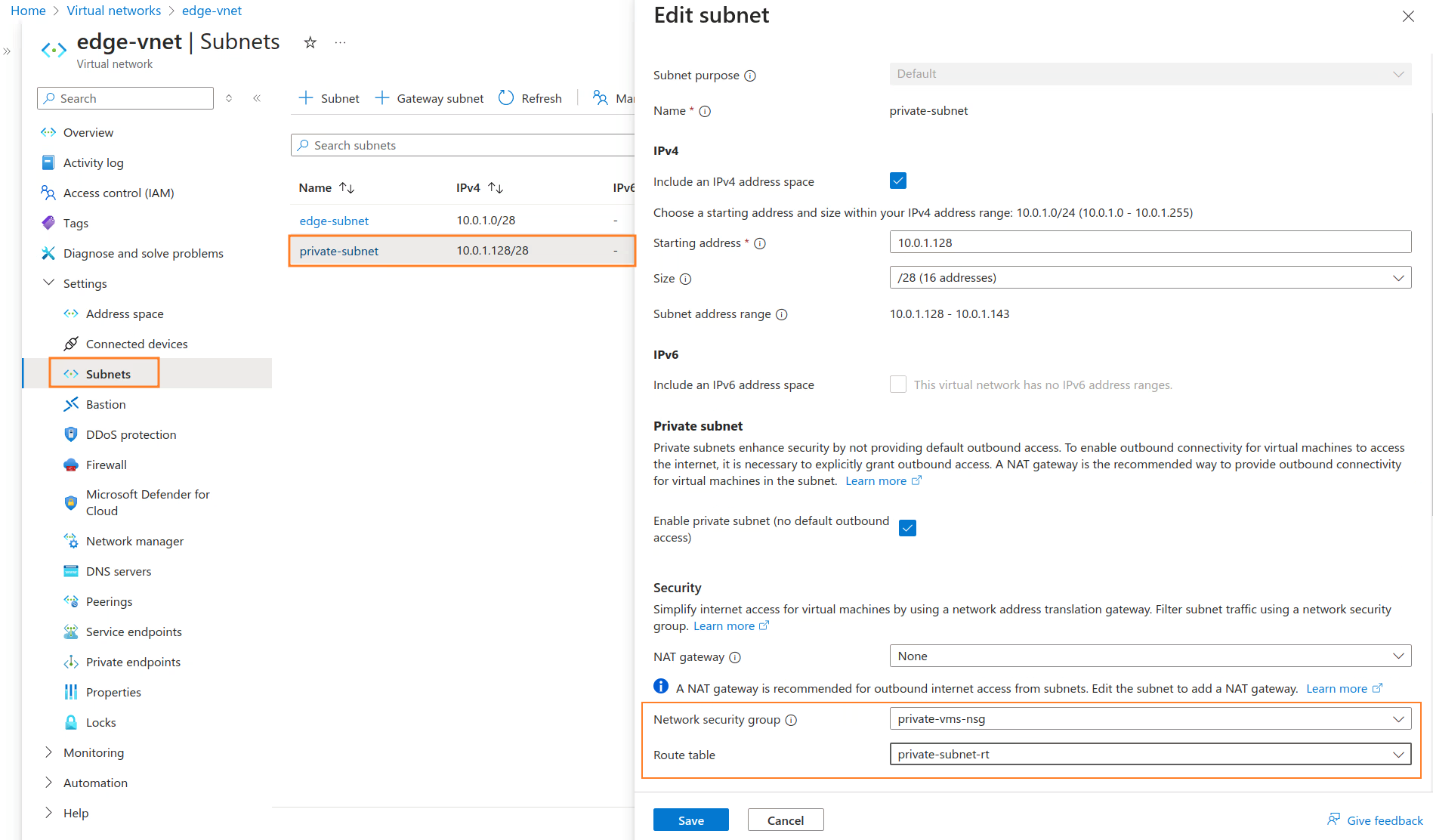
Now, we can create a Virtual Machine Scale Sets named private-vmss to automatically adjust the number of Virtual Machines based on demand.
The key configuration for the Virtual Machine Scale Sets is to associate it with the previously created resources. For more information on this process, refer to Create virtual machines in a scale set using Azure portal.
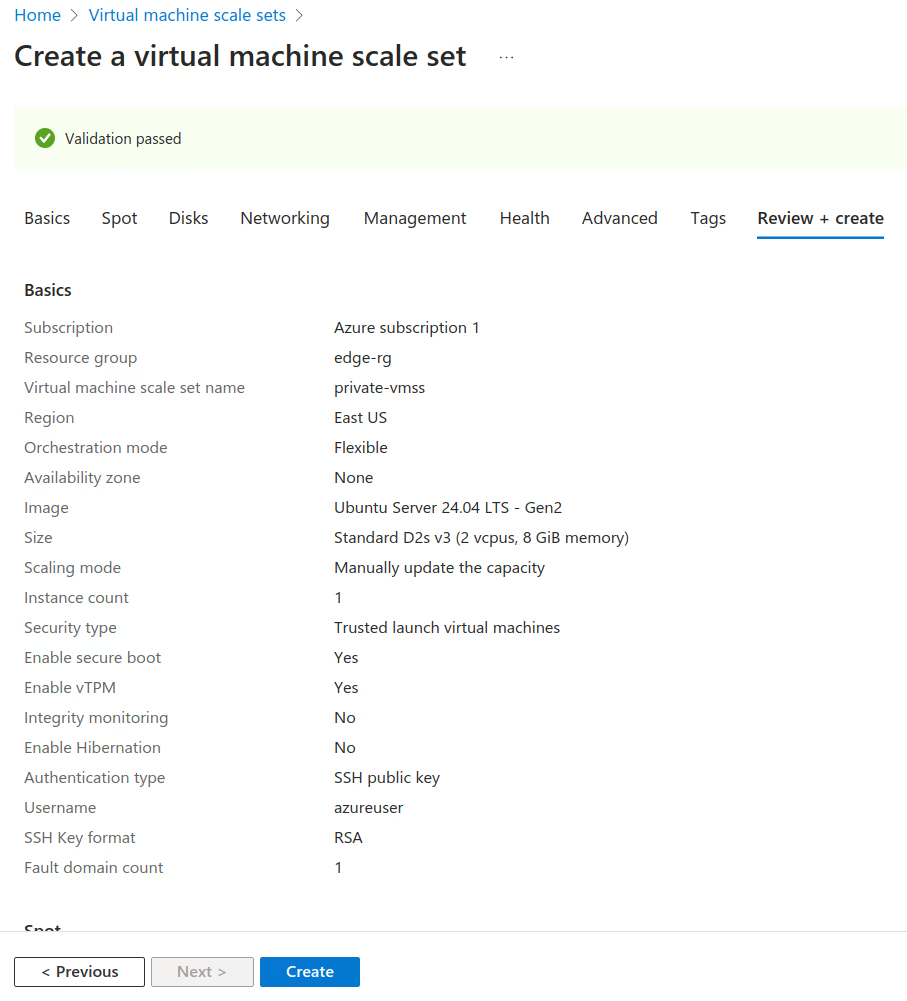
Note
During the configuration of Virtual Machine Scale Sets, a new Network Interface (NIC) named private-vm-nic must be created within the private-subnet in the networking section:
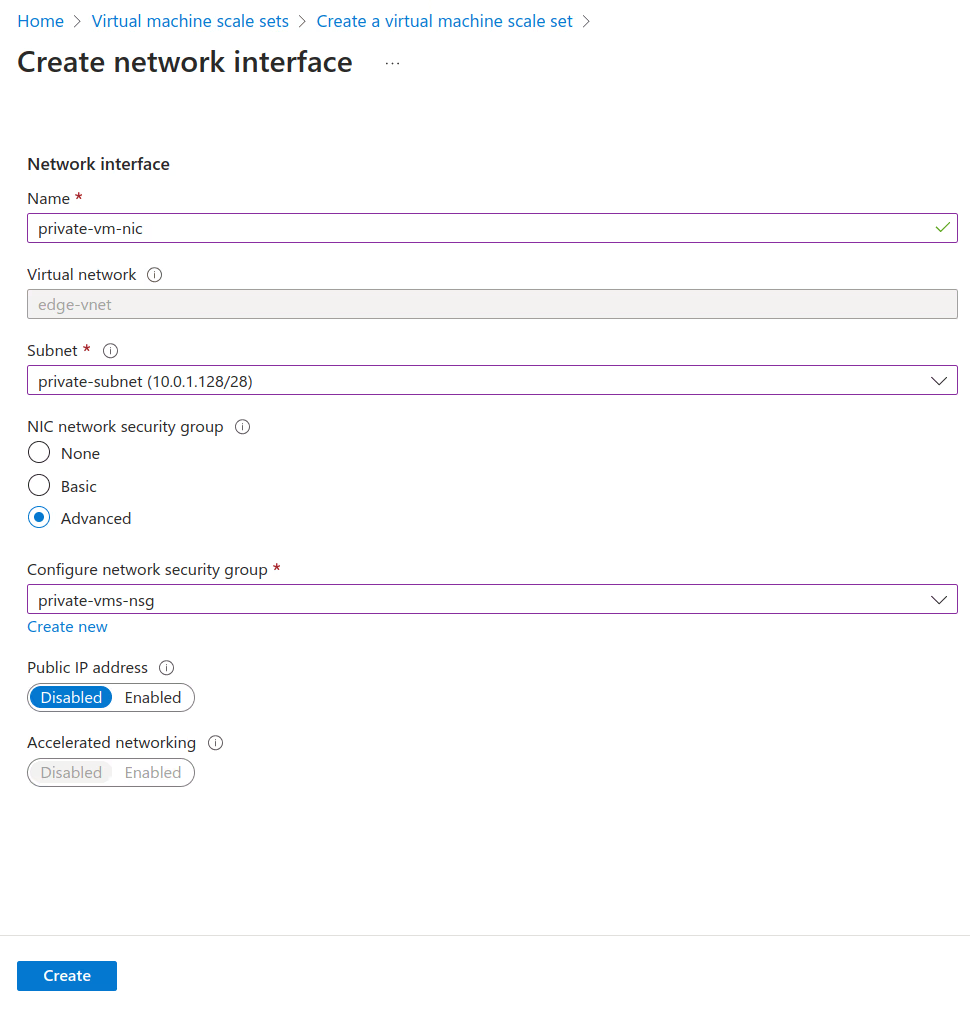
Once the Virtual Machine Scale Sets is configured, a new VM will be deployed in the private-subnet.
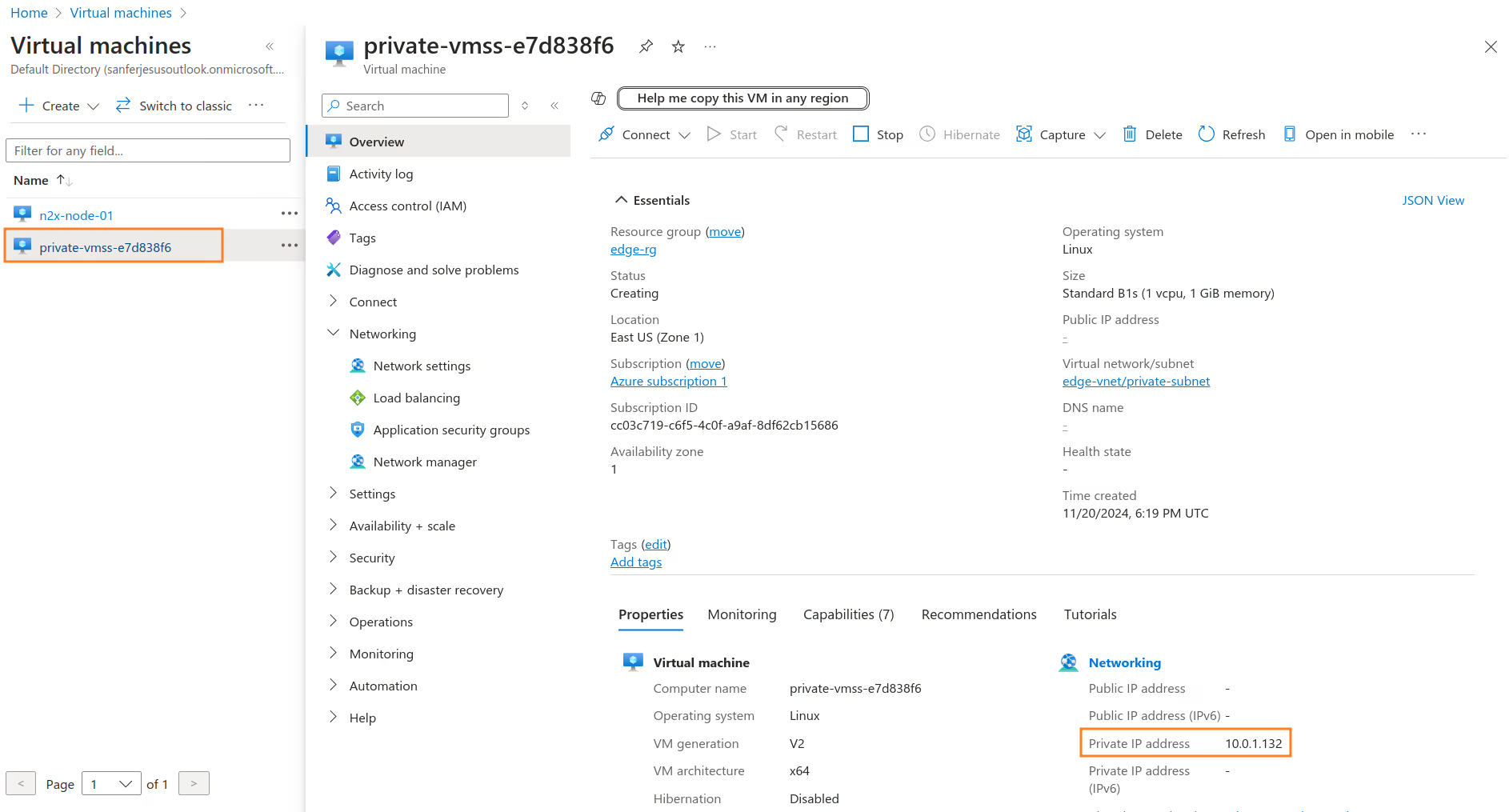
Note
The newly deployed Virtual Machine will be assigned a private IP address, such as 10.0.1.132 in this example. We'll use this private IP address to connect from server-01 during the validation step.
Step 4 - Connecting the server-01 to our n2x.io network topology
Now we need to connect the server-01 must be able to access the Virtual Machines.
Adding a new node in a subnet with n2x.io is very easy. Here's how:
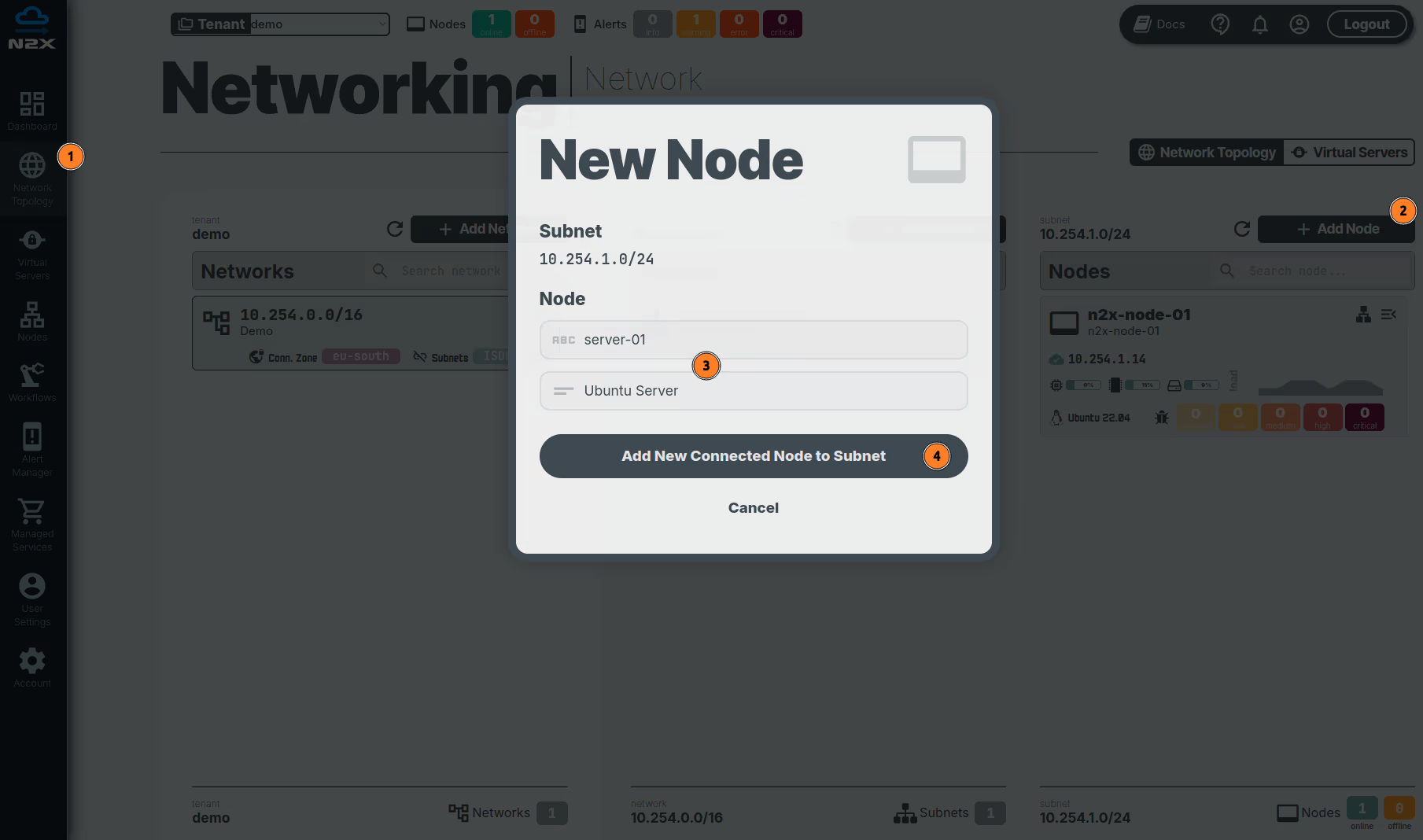
- Head over to the n2x WebUI and navigate to the
Network Topologysection in the left panel. - Click the
Add Nodebutton and ensure the new node is placed in the same subnet as then2x-node-01. - Assign a
nameanddescriptionfor the new node. - Click
Add New Connected Node to Subnet.
Here, we can select the environment where we are going to install the n2x-node agent. In this case, we are going to use Linux:
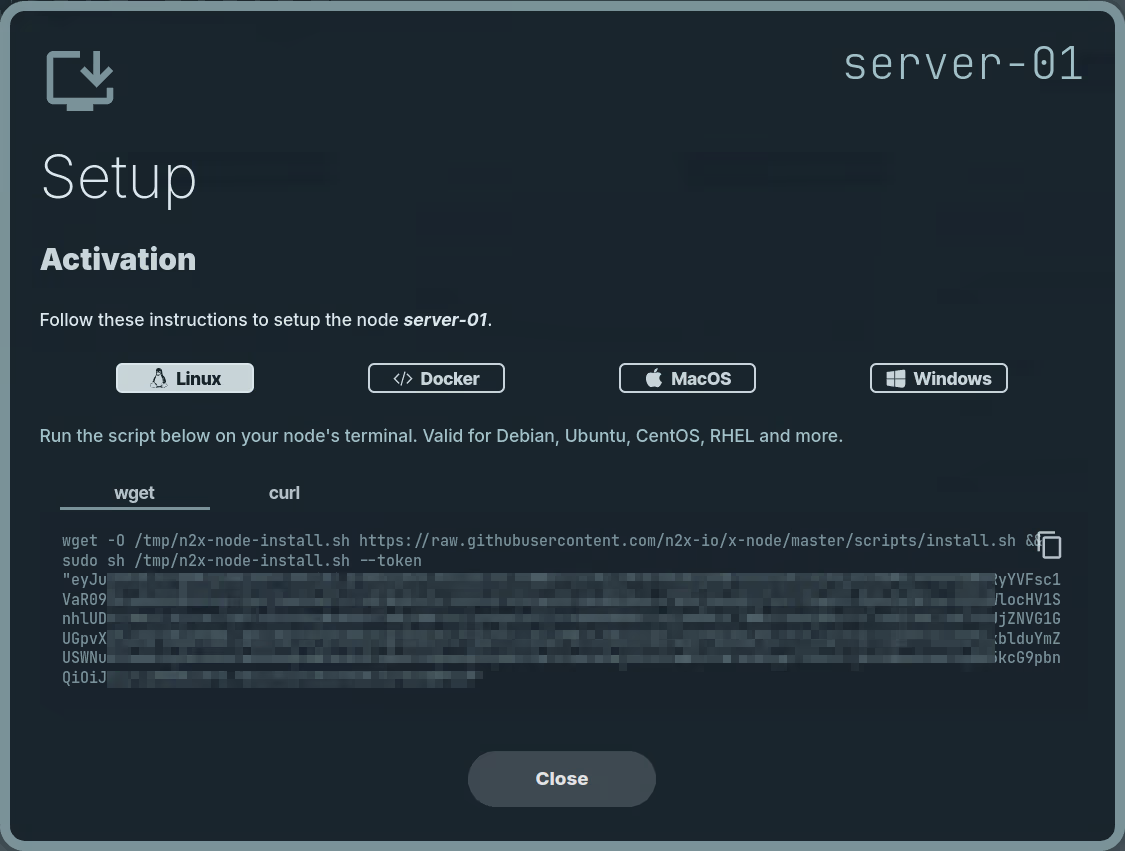
Run the script on server-01 terminal and check if the service is running with the command:
systemctl status n2x-node
You can use ip addr show dev n2x0 command on server-01 to check the IP assigned to this node:
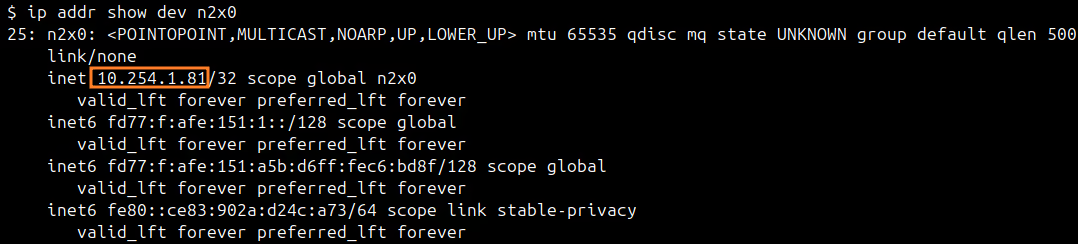
At this point, we need to make the VNet CIDR available in our server-01 importing this CIDR. For this, we need to edit /etc/n2x/n2x-node.yml in server-01 and add the following configuration:
# network routes behind this node (optional)
routes:
export:
-
import:
- <VNet CIDR>
Info
Replace <VNet CIDR> with the VNet CIDR value, in this case is 10.0.1.0/24.
Restart the n2x-node service for this change to take effect:
systemctl restart n2x-node
We can check the local routing table in server-01 with the following command:
ip route
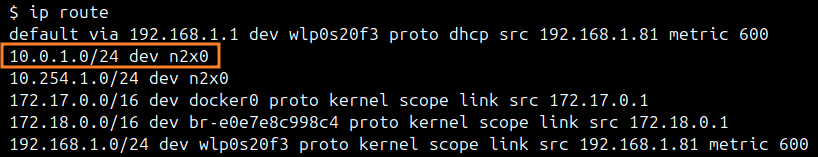
Step 5 - Verify your Connection
Once you've completed all configuration steps, you should be able to ping or connect via SSH to any Virtual Machine in the Azure VNet from any device connected to the n2x.io subnet.
We'll now verify connectivity to the Virtual Machine from server-01 device. In this scenario, the Virtual Machine has been assigned the private IP address 10.0.1.132.
Ping Test
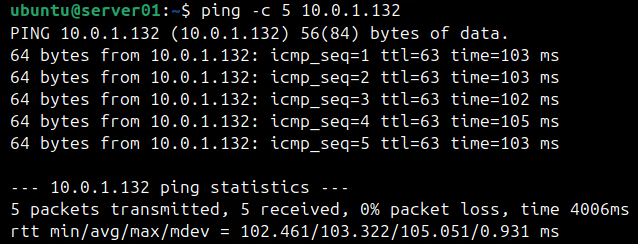
Let's first check if you can ping the Virtual Machine from server-01. Here's the command:
ping -c 5 10.0.1.132
SSH Connection
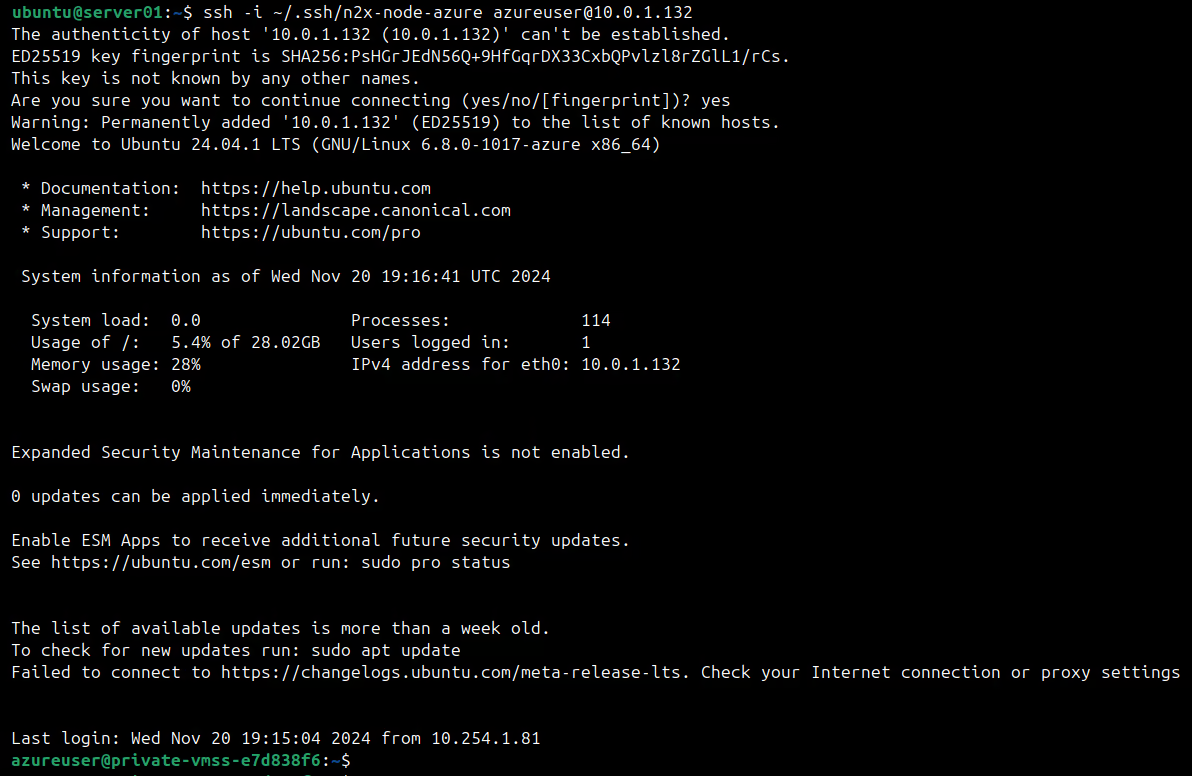
Now we can attempt an SSH connection to the Virtual Machine from server-01:
ssh -i ~/.ssh/n2x-node-azure [email protected]
Success
That's it! The Azure VNet is now accessible from any device connected to your n2x.io virtual private network.
Info
For even more granular control over traffic flow across your n2x.io network topology, explore n2x.io's security policies.
Conclusion
This article guided you through establishing a direct, secure connection between your n2x.io network topology and your Azure VNet.
This setup offers a secure, cost-effective, and streamlined approach to accessing your Azure VNet resources from your n2x.io network.