How to Deploy a n2x-node in Azure
This article offers a step-by-step guide on setting up a n2x-node in Azure, including creating all the necessary infrastructure within the cloud service provider.
Prerequisites
To complete this tutorial, you must meet the following requirements:
- An Azure account with an active subscription.
- A n2x.io account and one subnet with
10.254.1.0/24prefix.
Architecture
This section provides a basic architectural blueprint to guide you through deploying a n2x-node within the Azure cloud environment. This modular design offers versatility and can be reused for various deployment goals, including achieving High Availability (HA) for your n2x.io nodes within your network.
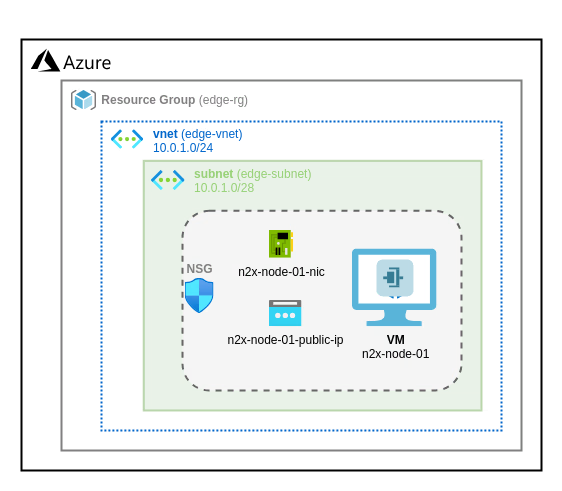
Step-by-step Guide
Step 1 - Creating and Configuring the Azure VNet
-
Create a resource group (edge-rg) to include the all resources we will create in the following steps. For more information, see Manage Azure resource groups by using the Azure portal.
-
Create the Virtual Network (VNet) using the values as described in the following table. For more information, see Virtual Network documentation.
VNet Settings
Resource Group Name IP Addresses edge-rg edge-vnet 10.0.1.0/24 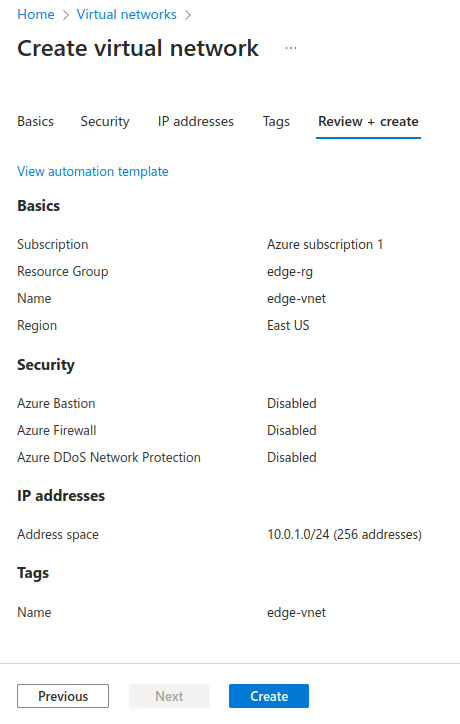
-
Add the subnet in the Vnet as described in the following table. For more information, see Add a Subnet.
Subnet Settings
Subnet Name IPv4 address range Starting address Size NAT gateway NSG Route table edge-subnet 10.0.1.0/24 10.0.1.0 /28 none none none 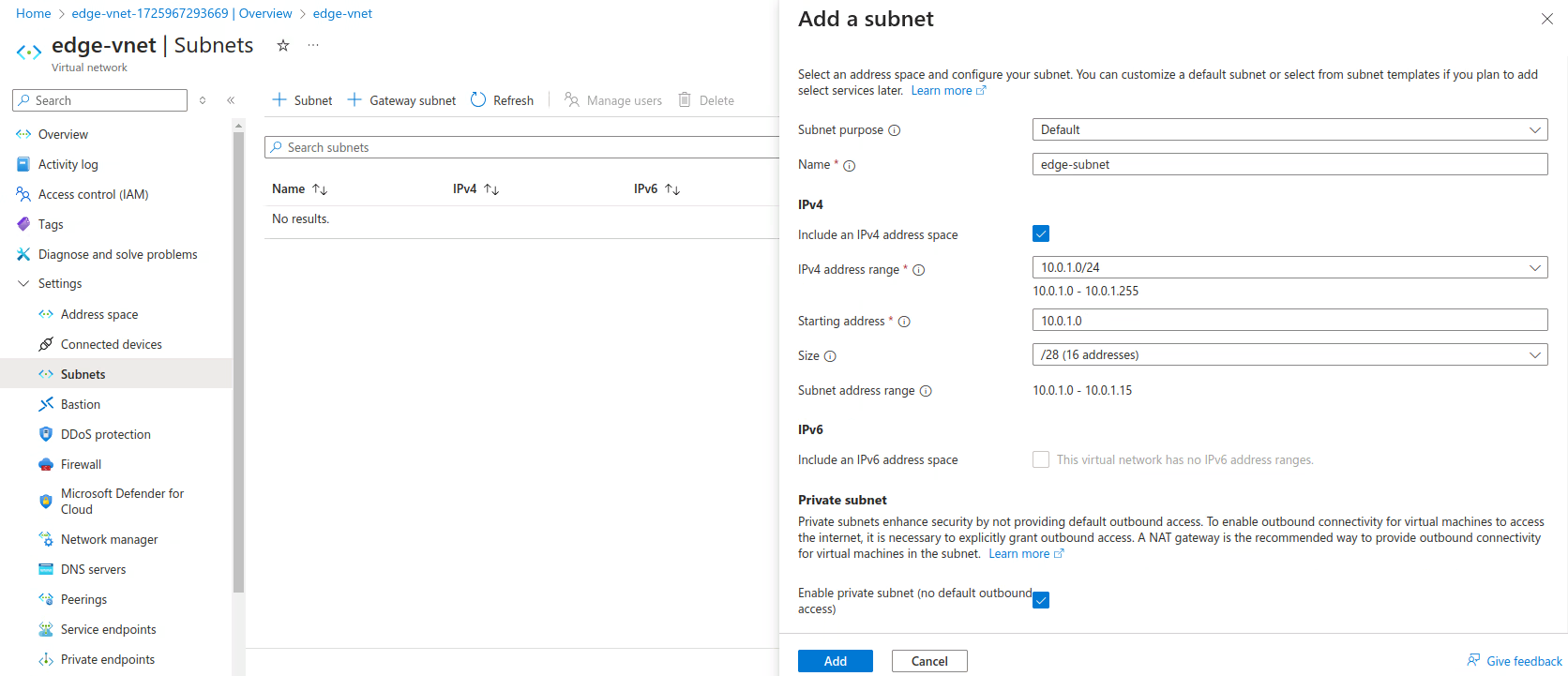
-
Create a new route table named
edge-rtand associate it with theedge-subnet. Then, add a default route with the destination0.0.0.0/0andInternetas Next Hop Type. For more information, see Manage Route Table.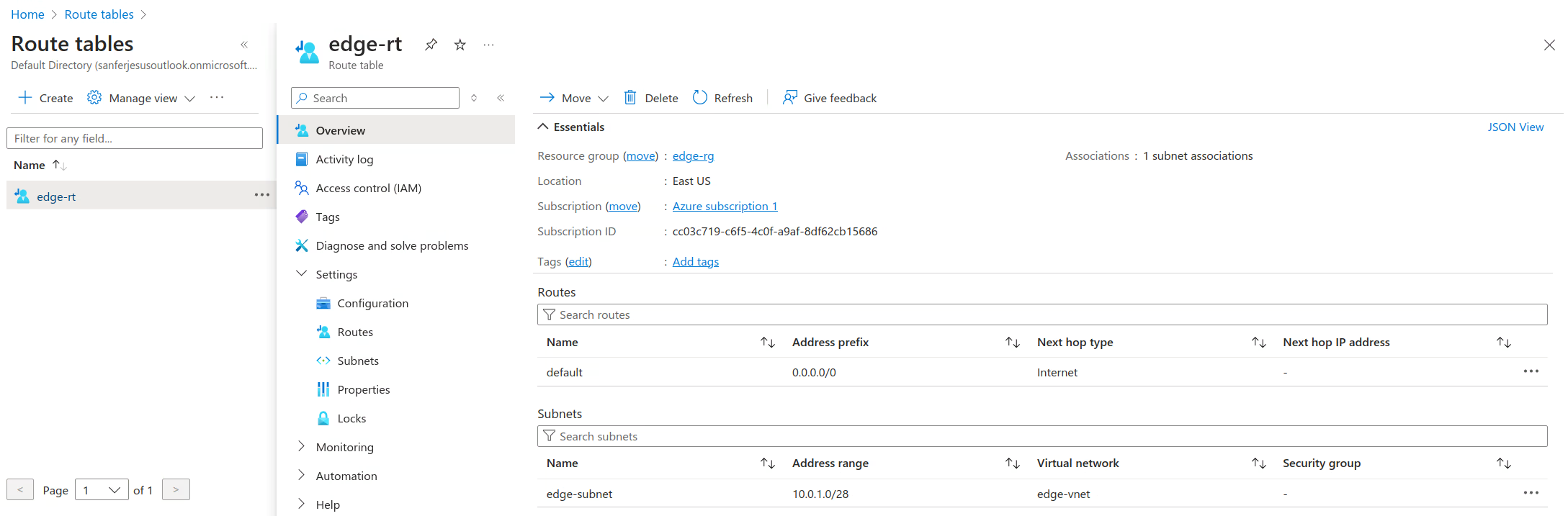
-
Create the Network Interface (NIC) using the values as shown in the following image. For more information, see Manage NICs
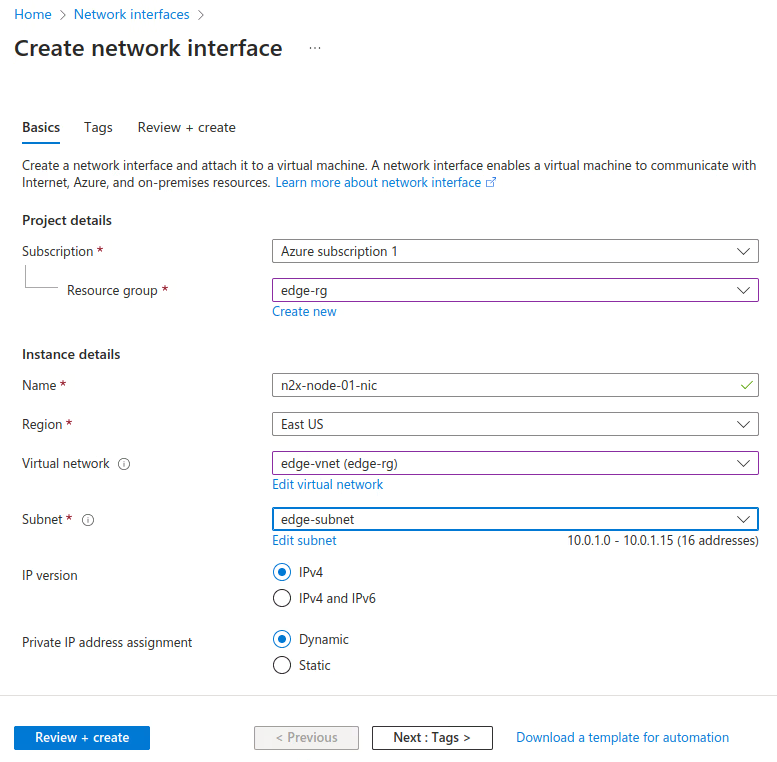
-
Create the Public IP address using the values as shown in the following image. For more information, see Create a public IP address.
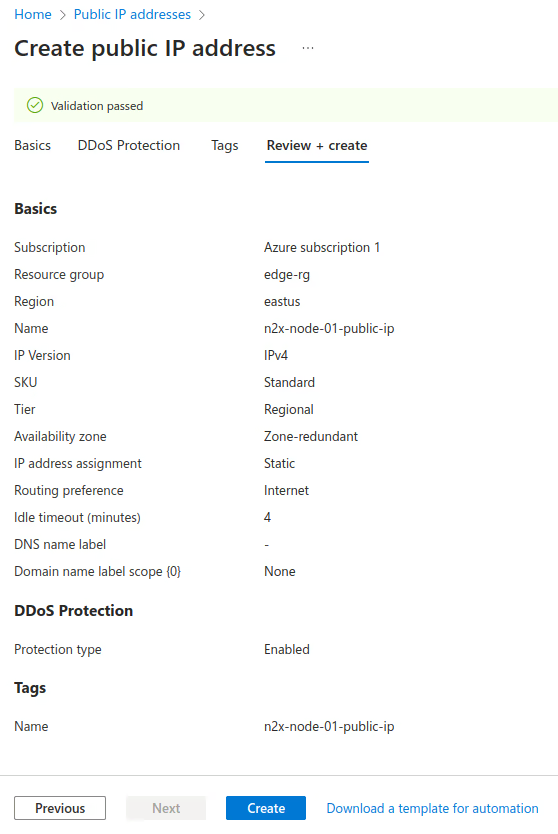
Associate the public IP address with the previously created interface:
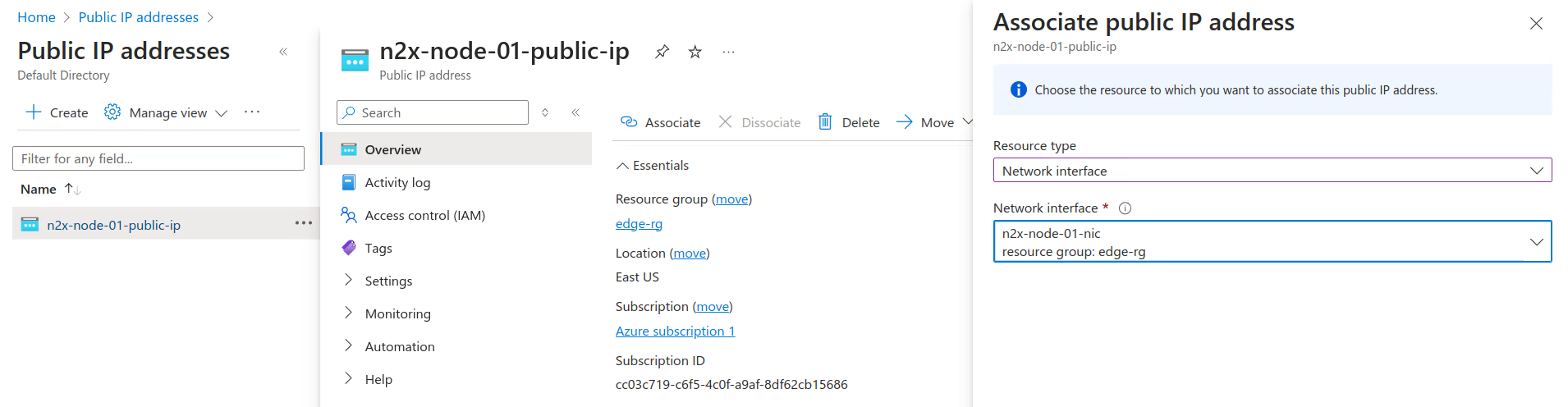
-
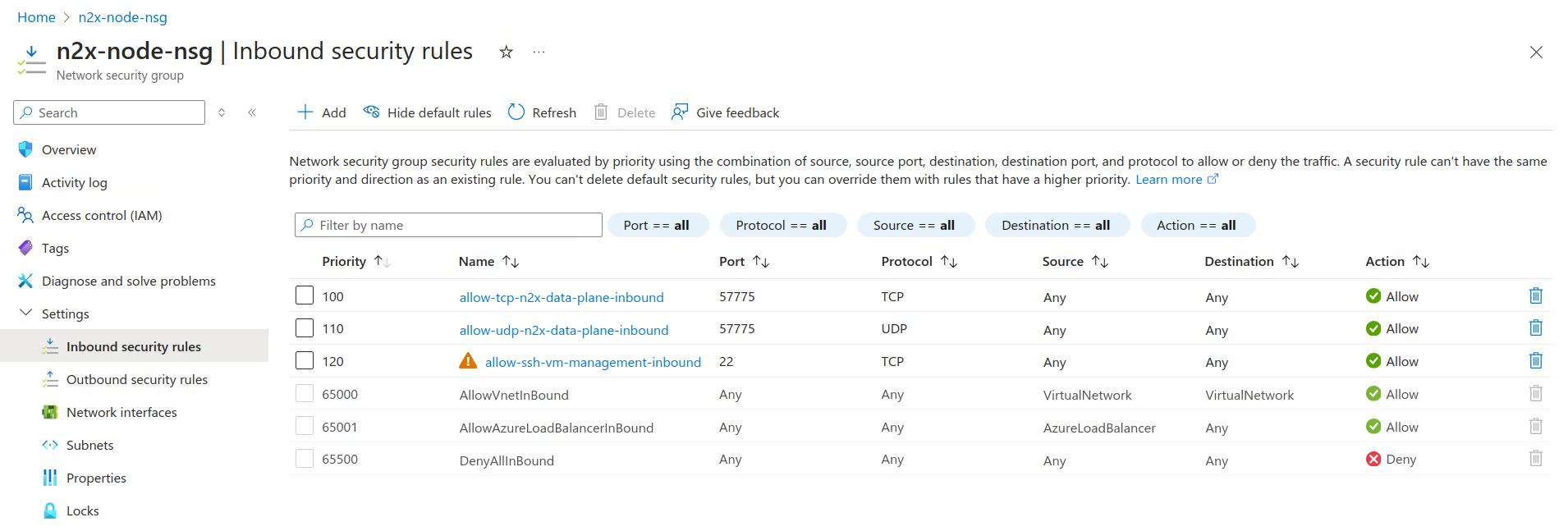
Create a network security group named n2x-node-nsg with minimal inbound and outbound security rules as described in the table below. For more information, see Manage network security groups.
Rule Source Source Port Range Destination Destination Port Range Protocol Name Inbound Any * Any 57775 TCP/UDP allow-tcp-n2x-data-plane-inbound Inbound Any * Any 22 TCP allow-ssh-vm-management-inbound Outbound Any * Any 443 TCP allow-https-n2x-control-plane-outbound Outbound Any * Any 1883 TCP allow-mqtt-n2x-control-plane-outbound Outbound Any * Any 57775 TCP/UDP allow-tcp-n2x-data-plane-outbound Info
For direct communication between n2x.io nodes, open inbound connections to ports 57775 TCP/UDP. (See direct connection for details).
Note
Open inbound connectivity to ports
SSHorRDP(or both) for remote VM management, as needed.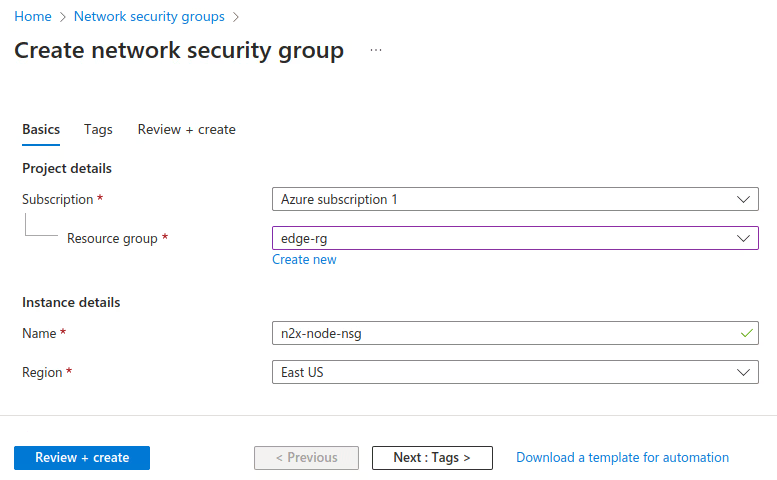
Associate the network security group with the previously created interface:
Step 2 - Creating a Virtual Machine
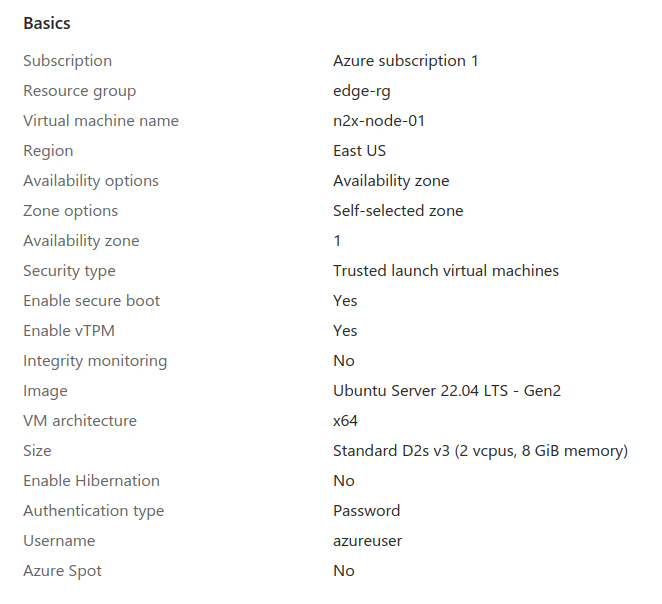
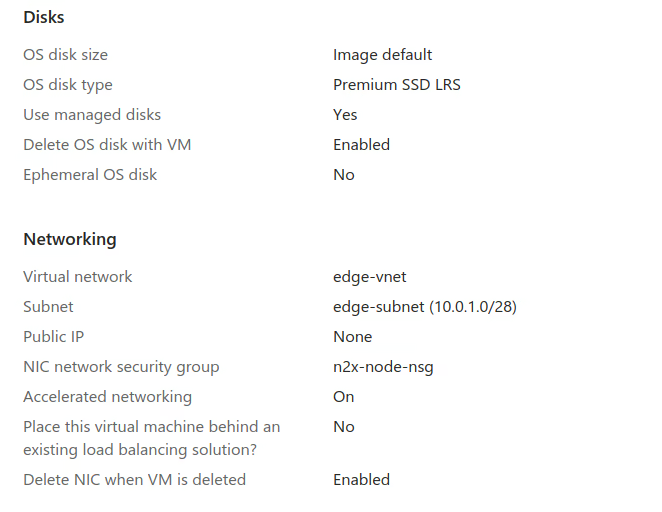
Create a Virtual Machine to support the n2x-node with the following configuration:
Note
Please note that this tutorial uses a Linux OS with an Ubuntu 22.04 (Jammy Jellyfish) but you can choose any OS supported by n2x.io and Azure instances.
Step 3 - Connecting VM to our n2x.io Network Topology
To connect your VM to the n2x.io network topology, you'll need to:
- Add a new connected node to your subnet.
- Install the n2x-node agent on the VM.
Step 4 - Verification
Let's confirm that everything is operational:
-
Check the
n2x-nodeservice status onn2x-node-01using:systemctl status n2x-node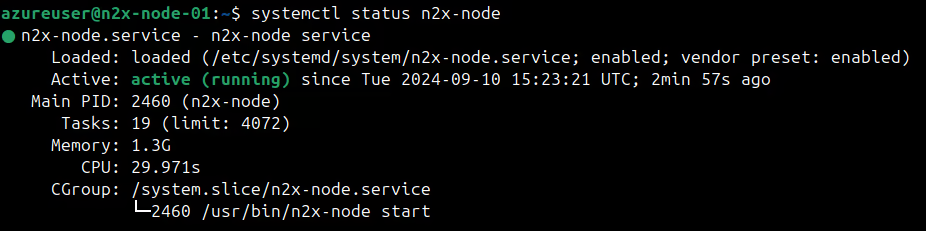
-
Verify that the
n2x0interface onn2x-node-01is active and has an IP address assigned by using the following command:ip addr show dev n2x0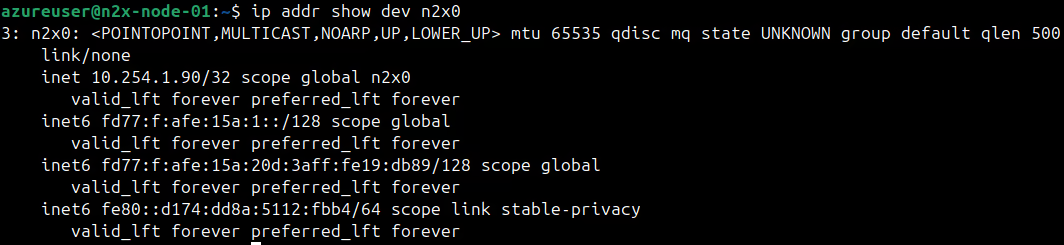
-
(Optional) To verify connectivity within the n2x.io subnet, you can perform a simple test if another node is present. In this example, we'll use
test-node-01which has the IP address10.254.1.209.ping -c 5 10.254.1.209
Conclusion
We've provided a comprehensive guide for launching a n2x-node in Azure. Feel free to adapt this foundation to meet your specific needs and implement more complex scenarios.