Securing a Windows RDP Connection for Remote Access
Remote Desktop Protocol (RDP) allows users to remotely control and interact with a computer as if they were physically present at the machine. This can be useful for various purposes, including technical support, troubleshooting, and accessing resources on a remote machine.
Remote Desktop Protocol (RDP) has been a common target for cyber attackers, including those deploying ransomware. The widespread use of RDP for legitimate remote access also makes it an attractive target for malicious actors looking to gain unauthorized access to systems.
One way to greatly reduce your attack surface is to avoid exposing your RDP to the Internet.
With n2x.io, you can allow only clients on your n2x.io network topology to connect to your RDP servers. n2x.io works transparently with the RDP client, securing your network without making RDP any harder to use.
Here is the high-level overview of the guide setup architecture:
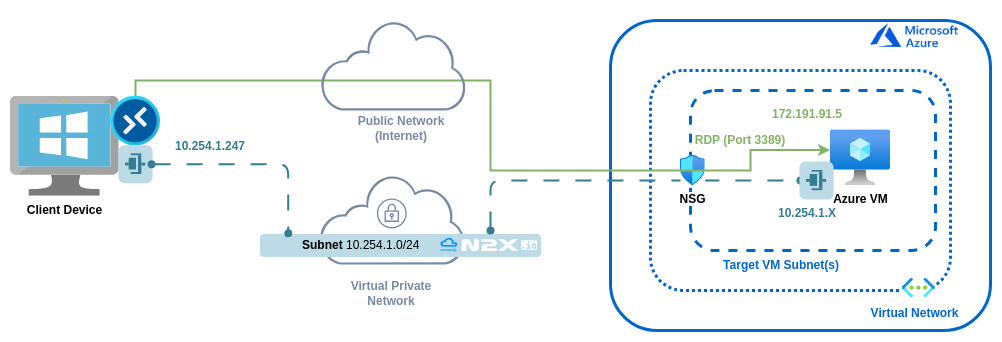
Before you begin
- This guide requires you to be on a Windows system that can serve as a Remote Desktop Server. If you do not have a remote Windows system, you can use Quickstart: Use Terraform to create a Windows VM in Azure.
- A n2x.io account created and one subnet with
10.254.1.0/24prefix.
Step-by-step Guide
Step 1: Connect Client Device to our n2x.io Network Topology
We need to connect Client Device to our n2x.io network topology to allow the connection to Azure VM privately.
Adding a new node in a subnet with n2x.io is very easy. Here's how:
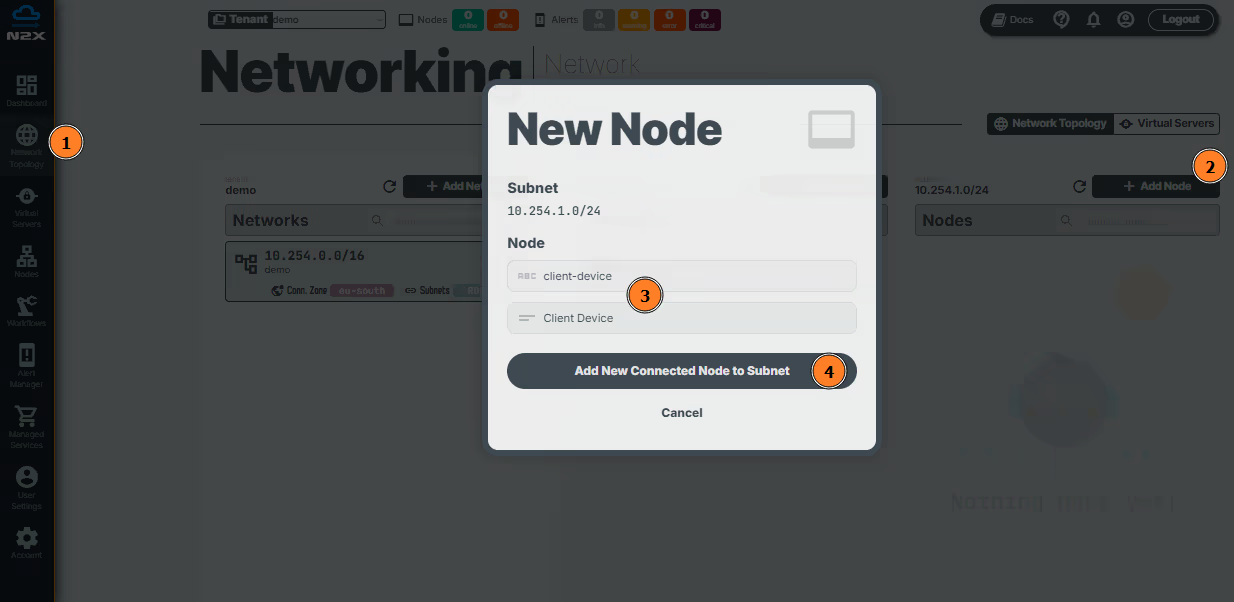
- Head over to the n2x.io WebUI and navigate to the
Network Topologysection in the left panel. - Click the
Add Nodebutton. - Assign a
nameanddescriptionfor the new node. - Click
Add New Connected Node to Subnet.
Here, we can select the environment where we are going to install the n2x-node agent. In this case, we are going to use Windows:
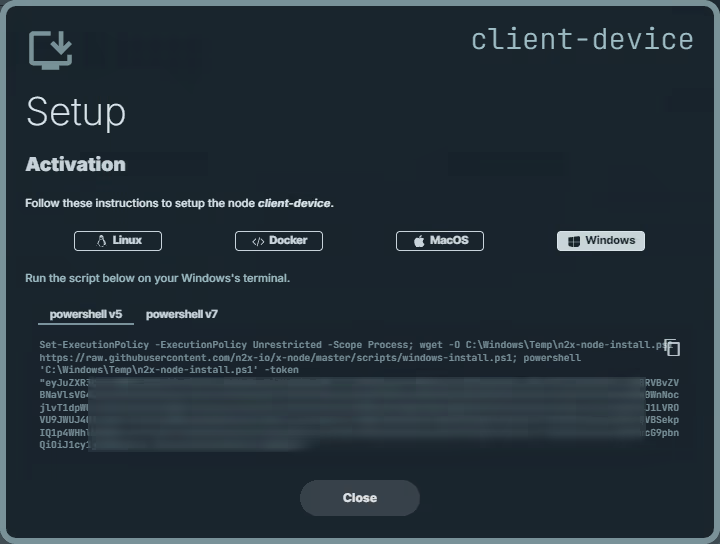
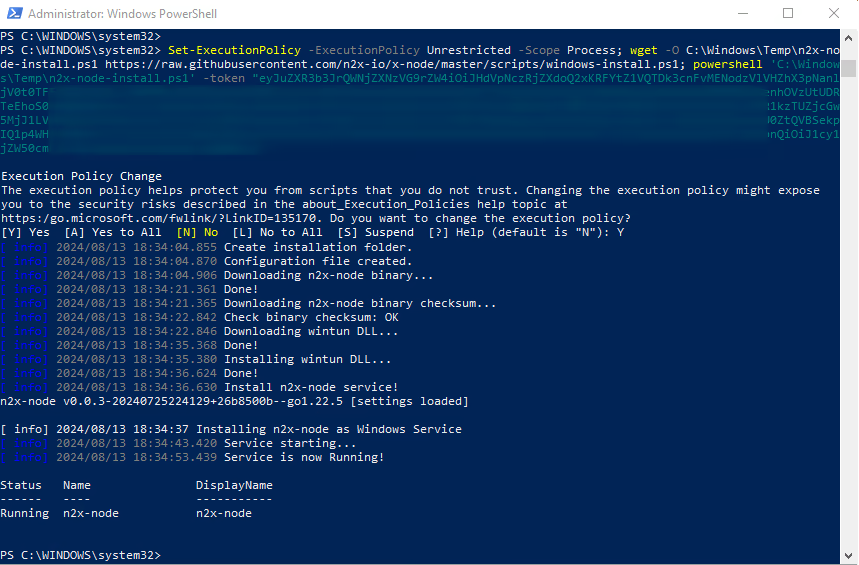
Open a Windows PowerShell as Administrator in Client Device and execute the previous one-line command:
You can use ipconfig command on Client Device to check the IP assigned to this node:
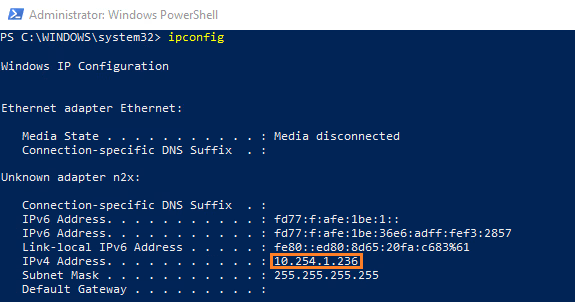
Step 2: Connect Azure VM to our n2x.io Network Topology
Now, we need to connect Azure VM to our n2x.io network topology to allow the connection from Client Device privately.
We are going to repeat the same steps as before. Here's how:
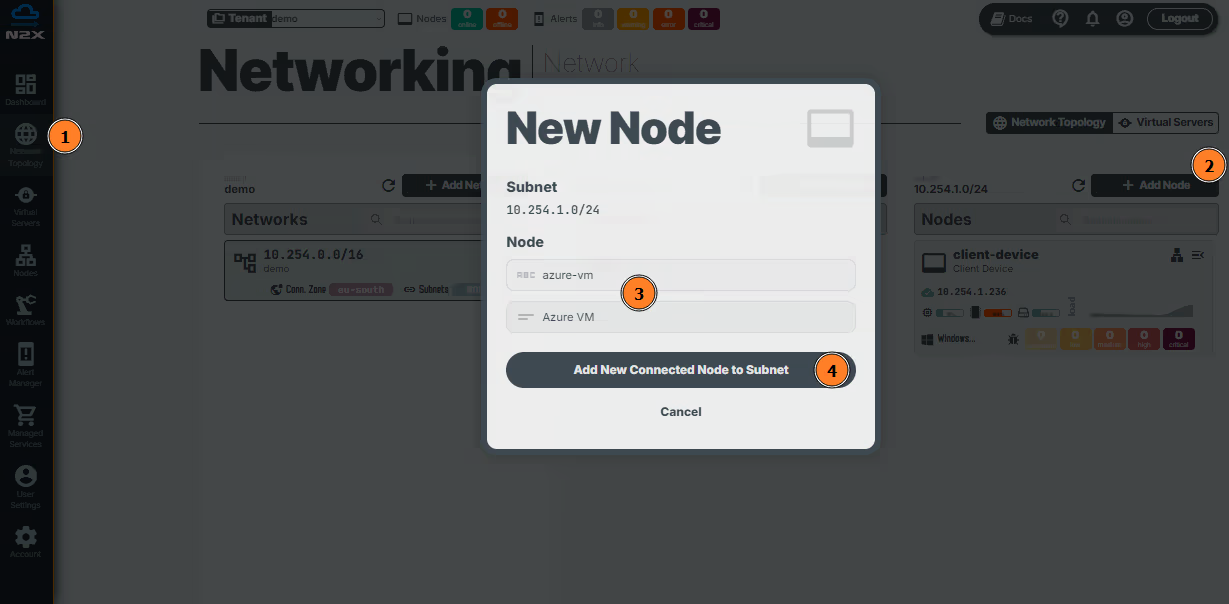
- Head over to the n2x.io WebUI and navigate to the
Network Topologysection in the left panel. - Click the
Add Nodebutton and ensure the new node is placed in the same subnet as theClient Device. - Assign a
nameanddescriptionfor the new node. - Click
Add New Connected Node to Subnet.
Here, we can select the environment where we are going to install the n2x-node agent. In this case, we are going to use Windows:
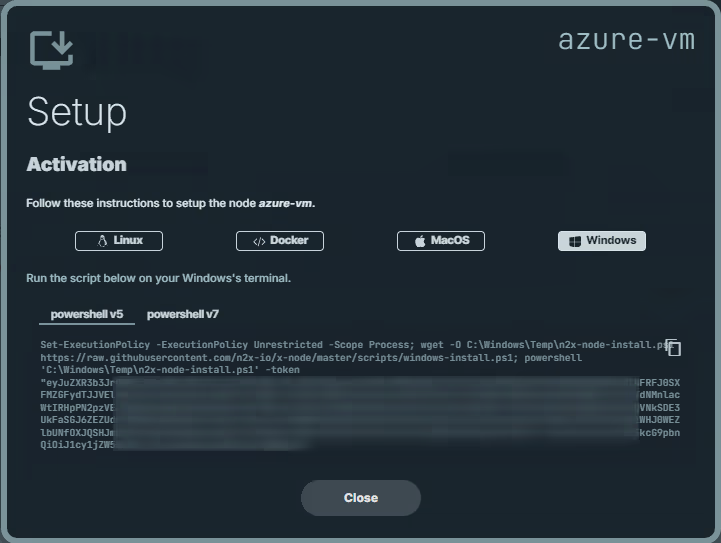
So we are going to connect to Azure VM via RDP through the public IP address, since we have not yet established n2x.io network topology:
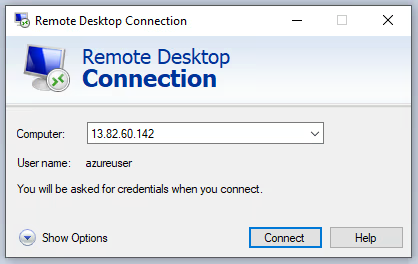
Open a Windows PowerShell as Administrator in Azure VM and execute the previous one-line command:
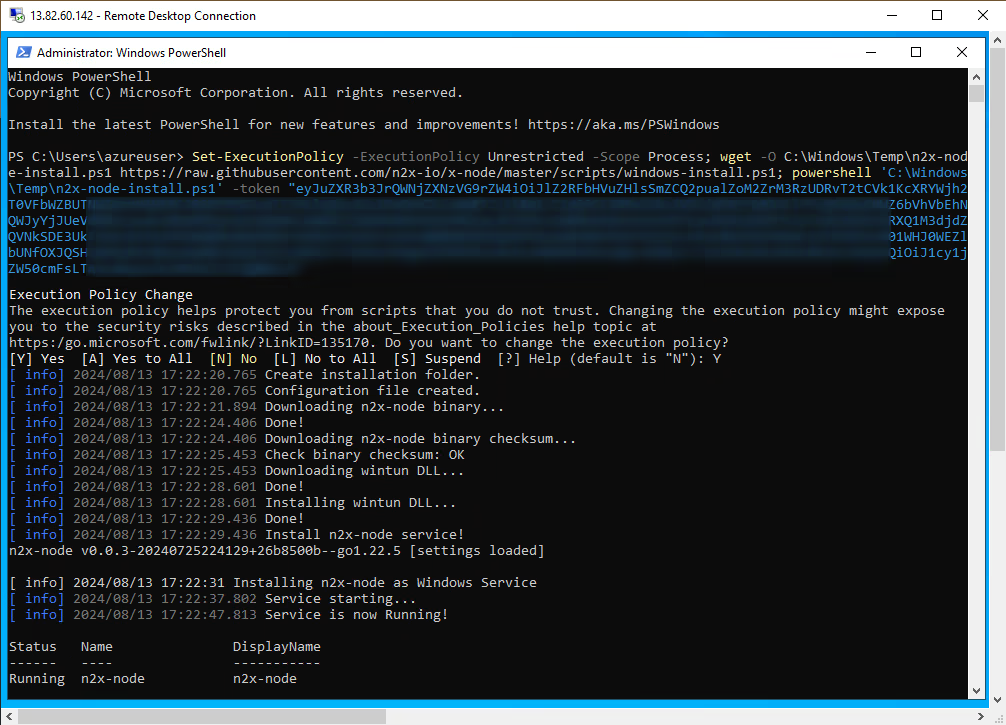
You can use ipconfig command on Azure VM to check the IP assigned to this node:
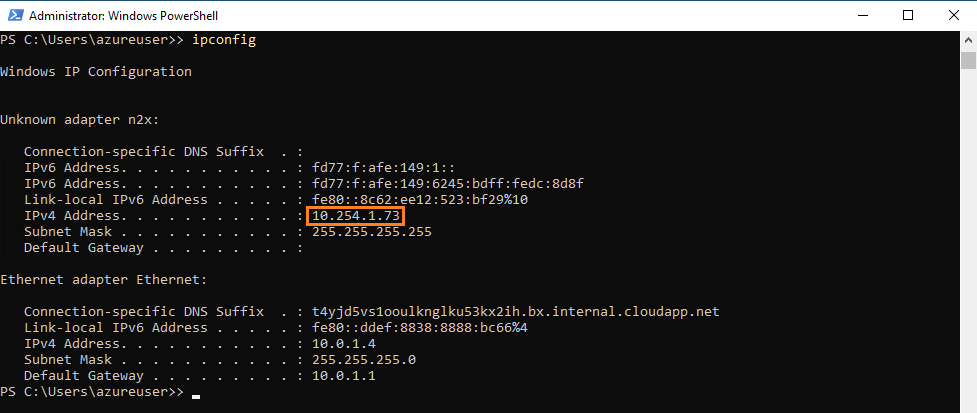
Step 3: Remove RDP Access from the Internet
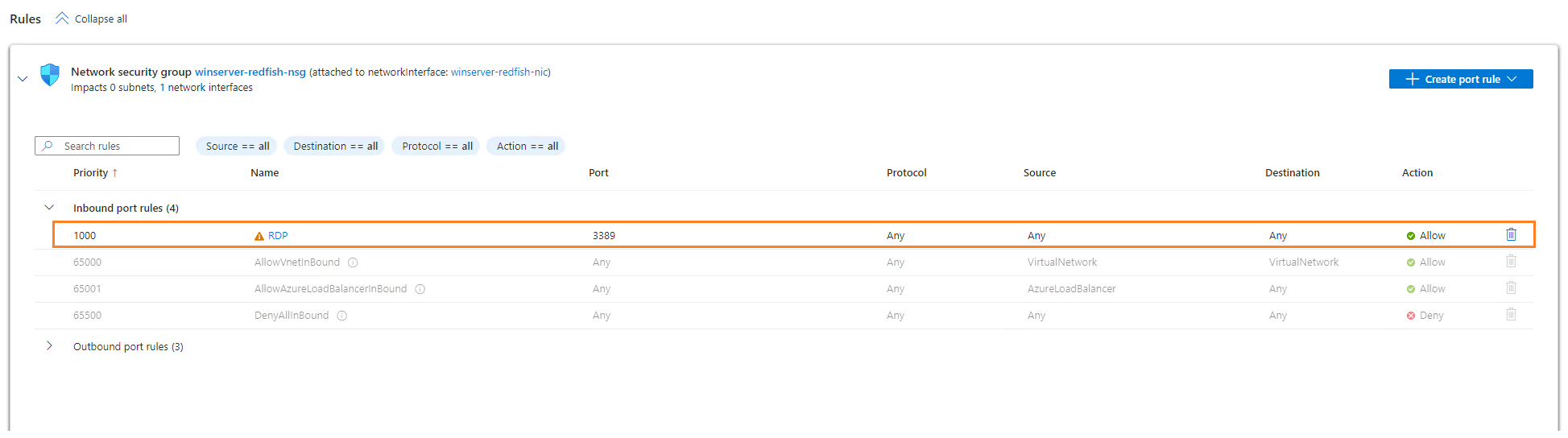
To remove RDP access the from Internet in the Azure VM, we are going to Select your VM > Networking > Network settings > Network security group and then remove RDP inbound port rules:
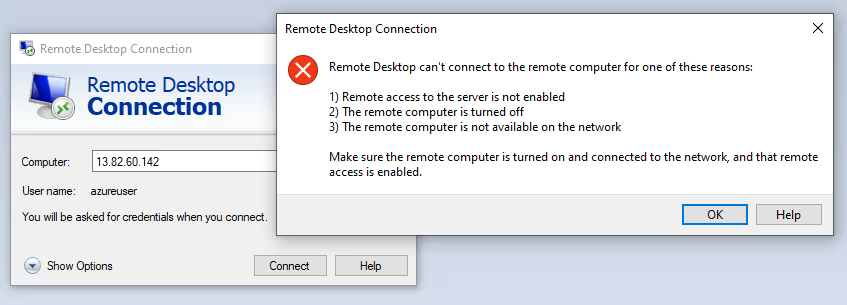
If we try to connect to Azure VM via RDP through the public IP, we will have the following error:
Step 4: Verify we can connect to Azure VM via RDP through our n2x.io Network Topology
And we’re done! Now we can verify that we can connect to Azure VM via RDP from Client Device through our n2x.io network topology. So we are going to connect to Azure VM via RDP through the 10.254.1.73 IP address assigned by n2x.io IPAM:
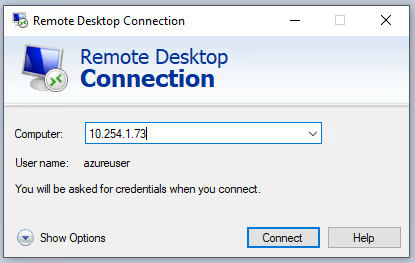
Success
That's it! At this point, any node on your n2x.io network should be able to access Azure VM.
Note
For even more granular control over traffic flow across your n2x.io network topology, explore n2x.io's security policies.
Conclusion
In this guide, we've learned how n2x.io can help to avoid exposing RDP to the Internet. So organizations can significantly reduce the risk of RDP-related security incidents and protect their systems from ransomware attacks and other forms of exploitation.